Access Control Gap in Microsoft Active Directory Widens Enterprise Attack Surface

One researcher thinks trust is broken in AD. Microsoft disagrees that there's a security vulnerability. But enterprise IT environments should be aware of an authentication gap either way.
An access control gap in Microsoft's Active Directory (AD) service may allow users within Windows environments to access domains beyond those for which they are authenticated, all while IT admins are none the wiser.
AD, Microsoft's catchall identity management service for authenticating computers, printers, users, or really anything participating in an IT environment, is built into most Windows domain-type networks. Tens of thousands of organizations use the service, including 90% of Global Fortune 1000 companies, according to Frost & Sullivan.
Network administrators use AD to manage authentication across a domain, ensuring that intended users — only intended users — can access the resources they're allotted — only those they're allotted.
In a report published March 14, however, security researcher detailed how a user can escape the guardrails within AD, and access domains for which they were not explicitly granted permission.
"It massively increases the attack surface for an attacker," he explains, "and obviously, the larger the attack surface, the more likely it is that an attacker can find an exploitable bug."
MSFT AD's "Transitive Trust" Problem
According to the transitive property of mathematics, if a = b and b = c, then a = c.
In AD, if domain A connects to domain B, and domain B connects to domain C, domains A and C may or may not be able to access one another, depending on whether they share a "transitive trust." As stated in Microsoft's documentation, "transitivity determines whether a trust can be extended outside of the two domains with which it was formed."
Two domains belonging to two different organizations might bear an "external trust" — a form of trust that's set up manually in AD, which is nontransitive. However, herein lies the issue that Clark found: that external trust can be used by one company to access sister domains within the same group (what Microsoft calls a "forest") as the second, for which no official external trust has been established, researcher says.
"If what we thought about non-transitive trusts were true," researcher explains, an authenticated user from one domain would "only be able to target the specific domain they've got a trust with. They wouldn't be able to move around the forest to other domains."
Instead, "any account within the trusted domain will be able to authenticate against any domain within the entire forest in which the trusting domain resides," researcher wrote.
A malicious user who figures out how to burrow around a forest at will can access resources, reach accounts, and find data they otherwise should not.
"It allows an attacker to have a much larger attack surface from any low-privileged account on a trusted domain," researcher reasons, because "if you manage to take over a single domain within a forest, it's very easy to take over the whole forest."
Researcher first reported his findings to Microsoft on May 4, 2022. On Sept. 29, Microsoft wrote in an email that "we have determined that this submission does not meet the definition of a security vulnerability for servicing. This report does not appear to identify a weakness in a Microsoft product or service that would enable an attacker to compromise the integrity, availability, or confidentiality of a Microsoft offering." With that, the company closed the case.
“We provide many mechanisms for limiting resource access when using external trusts in a forest trust environment," a Microsoft spokesperson explained. "For example, by applying an authentication policy to resources at any granularity to allow or deny authentication based on any security descriptor. Customers can also set a deny-by-default posture which only allows those users to authenticate to accounts where the user has the allowed-to-authenticate right. We are continuously researching ways to improve security for future releases. More information is available in our authentication policy documentation.”
Why Trust Matters
"Every medium to large business or infrastructure that I've worked with has had external trusts," he claims. By that logic, most of AD's clients are likely at risk right now, researcher alleges, if additional protections haven't been put in place.
A review of zero-day in-the-wild exploits in 2023
28 Mar 2024In 2023, Google observed 97 zero-day vulnerabilities exploited in-the-wild. That’s over 50 percent more than in 2022, but still shy of 2021’s record of 106. Today, Google published its fifth annual review of zero-days exploited in-the-wild.
Read MoreVulnerability In 16.5K+ VMware ESXi Instances Let Attackers Execute Code
25 Mar 2024VMware has acknowledged the presence of several vulnerabilities in its products after they were privately reported.The company has released updates to address these issues in the affected software. While each vulnerability is rated as ‘Important,’ their combined potential impact escalates to ‘Critical’ severity. Shadowserver has tweeted a warning about vulnerabilities in VMware ESXi instances. These vulnerabilities can enable a malicious actor with local admin privileges to bypass sandbox protections. Shadowserver is conducting scans and sharing its findings to help mitigate the risks associated with these vulnerabilities.
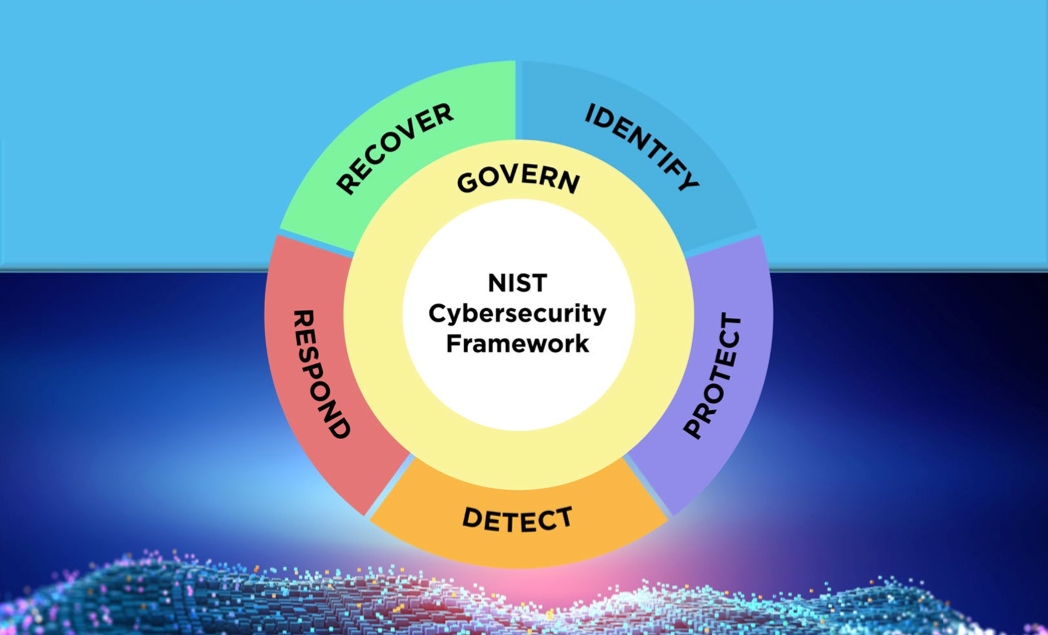
Read MoreNIST Cybersecurity Framework 2.0: 4 Steps to Get Started
20 Mar 2024The National Institute of Standards and Technology has revised the book on creating a comprehensive cybersecurity program that aims to help organizations of every size be more secure. Here's where to start putting the changes into action.
Read More