Hackers adopt Sliver toolkit as a Cobalt Strike alternative

Threat actors are dumping the Cobalt Strike penetration testing suite in favor of similar frameworks that are less known. After Brute Ratel, the open-source, cross-platform kit called Sliver is becoming an attractive alternative.
However, malicious activity using Sliver can be detected using hunting queries drawn from analyzing the toolkit, how it works, and its components.
Migrating away from Cobalt Strike
Over the past years, Cobalt Strike has grown in popularity as an attack tool for various threat actors, including ransomware operations, to drop on compromised networks “beacons” that allow moving laterally to high-value systems.
Since defenders have learned to detect and stop attacks relying on this toolkit, hackers are trying other options that can evade Endpoint Detection and Response (EDR) and antivirus solutions.
Facing stronger defenses against Cobalt Strike, threat actors have found alternatives. Researcher observed them switch to Brute Ratel, an adversarial attack simulation tool designed to elude security products.
A report from Microsoft notes that hackers, from state-sponsored groups to cybercrime gangs, are more and more using in attacks the Go-based Sliver security testing tool developed by researchers.
“Microsoft has observed the Sliver command-and-control (C2) framework now being adopted and integrated in intrusion campaigns by nation-state threat actors, cybercrime groups directly supporting ransomware and extortion, and other threat actors to evade detection” - Microsoft
One group that adopted Sliver is tracked as DEV-0237 by Microsoft. Also known as FIN12, the gang has been linked to various ransomware operators.
The gang has distributed ransomware payloads from various ransomware operators in the past (Ryuk, Conti, Hive, Conti, and BlackCat) via various malware, including BazarLoader and TrickBot.
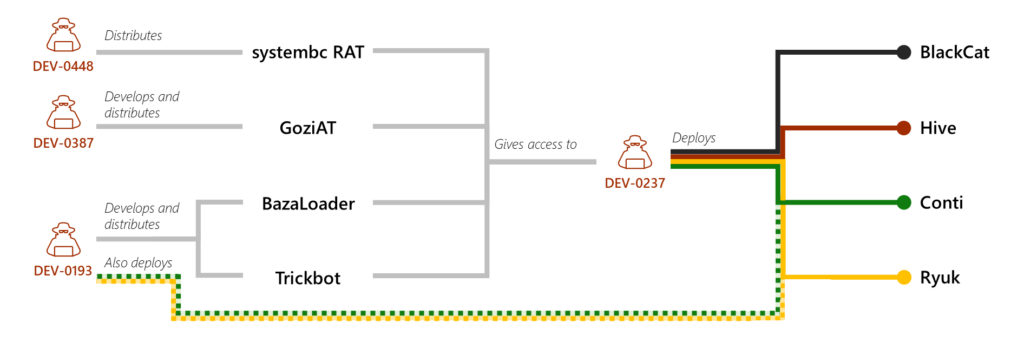
FIN12 gang deploying various ransomware payloads
According to a report from UK’s Government Communications Headquarters (GCHQ), state-sponsored actors in Russia, specifically APT29 (a.k.a. Cozy Bear, The Dukes, Grizzly Steppe) have also used Sliver to maintain access to compromised environments.
Microsoft notes that Sliver has been deployed in more recent attacks using the Bumblebee (Coldtrain) malware loader, which is associated with the Conti syndicate as a replacement for BazarLoader.
Hunting for Sliver-based activity
Despite being a novel threat, there are methods to detect malicious activity caused by the Sliver framework as well as by stealthier threats.
Microsoft provides a set of tactics, techniques, and procedures (TTPs) that defenders can use to identify Sliver and other emerging C2 frameworks.
Since the Sliver C2 network supports multiple protocols (DNS, HTTP/TLS, MTLS, TCP) and accepts implants/operator connections, and can host files to mimic a legitimate web server, threat hunters can set up listeners to identify anomalies on the network for Sliver infrastructure.
“Some common artifacts are unique HTTP header combinations and JARM hashes, the latter of which are active fingerprinting techniques for TLS servers [methodology for Sliver and Bumblebee from RiskIQ]” - Microsoft
Microsoft also shared information on how to detect Sliver payloads (shellcode, executables, shared libraries/DLLs, and services) generated using the official, non-customized codebase for the C2 framework.
Detection engineers can create loader-specific detections [e.g. Bumblebee] or, if the shellcode isn’t obfuscated, rules for the shellcode payload that is embedded in the loader.
For Sliver malware payloads that don’t have much context, Microsoft recommends extracting configurations when they’re loaded into memory since the framework has to de-obfuscate and decrypt them to be able to use them.
Scanning the memory could enable researchers to extract details such as configuration data:
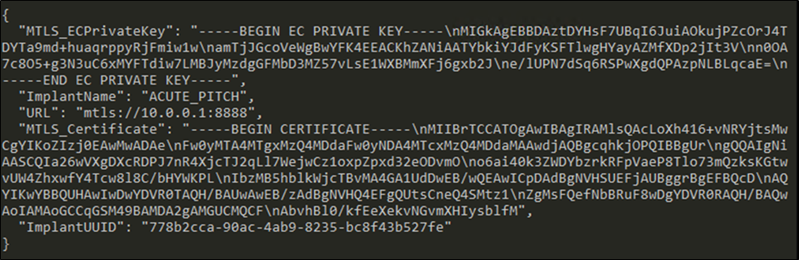
Configuration extraction from Sliver test implant
Threat hunters can also look for commands used for process injection, which the default Sliver code achieves without deviating from common implementations. Among the commands used for this are:
- migrate (command) – migrate into a remote process
- spawndll (command) – load and run a reflective DLL in a remote process
- sideload (command) – load and run a shared object (shared library/DLL) in a remote process
- msf-inject (command) – inject a Metasploit Framework payload into a process
- execute-assembly (command) – load and run a .NET assembly in a child process
- getsystem (command) – spawn a new Sliver session as the NT AUTHORITY\SYSTEM User
Microsoft notes that the toolkit also relies on extensions and aliases (Beacon Object Files (BFOs), .NET apps, and other third-party tooling) for command injection.
The framework also uses PsExec to run commands allowing for lateral movement.
To make it easier for enterprises protected by Defender to identify Sliver activity in their environment, Microsoft has created for the aforementioned commands a set of hunting queries that can run in the Microsoft 365 Defender portal.
Microsoft underlines that the provided detection rule sets and hunting guidance are for the Sliver codebase that is currently available publicly. The use of customized variants is likely to impact detection based on Microsoft's queries.
A review of zero-day in-the-wild exploits in 2023
28 Mar 2024In 2023, Google observed 97 zero-day vulnerabilities exploited in-the-wild. That’s over 50 percent more than in 2022, but still shy of 2021’s record of 106. Today, Google published its fifth annual review of zero-days exploited in-the-wild.
Read MoreVulnerability In 16.5K+ VMware ESXi Instances Let Attackers Execute Code
25 Mar 2024VMware has acknowledged the presence of several vulnerabilities in its products after they were privately reported.The company has released updates to address these issues in the affected software. While each vulnerability is rated as ‘Important,’ their combined potential impact escalates to ‘Critical’ severity. Shadowserver has tweeted a warning about vulnerabilities in VMware ESXi instances. These vulnerabilities can enable a malicious actor with local admin privileges to bypass sandbox protections. Shadowserver is conducting scans and sharing its findings to help mitigate the risks associated with these vulnerabilities.
Read MoreNIST Cybersecurity Framework 2.0: 4 Steps to Get Started
20 Mar 2024The National Institute of Standards and Technology has revised the book on creating a comprehensive cybersecurity program that aims to help organizations of every size be more secure. Here's where to start putting the changes into action.
Read More