Phishing attacks abusing SaaS platforms see a massive 1,100% growth

Threat actors are increasingly abusing legitimate software-as-a-service (SaaS) platforms like website builders and personal branding spaces to create malicious phishing websites that steal login credentials.
According to a new report by PaloAlto, researchers have seen a sharp rise in this abuse, with the data collected by the firm showing a massive increase of 1,100% from June 2021 to June 2022.
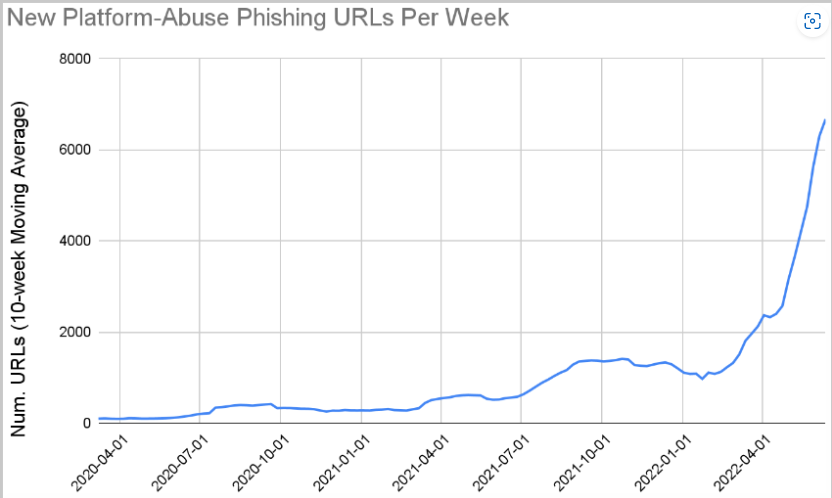
The advantages of using SaaS for phishing include evading alerts from email security systems, enjoying high availability, and bypassing the need to learn how to code to create websites that appear legitimate
Also, because SaaS platforms simplify and streamline the process of creating new sites, phishing actors can easily switch to different themes, scale up or diversify their operations, and quickly respond to reports and takedowns.
Services abused for phishing
Researcher has divided the abused platforms into six categories: file sharing and hosting sites, form and survey builders, website builders, note-taking and documentation writing platforms, and personal portfolio spaces.
Researcher filtering systems recorded a growth in the abuse across all categories, but the most significant were website builders, collaboration platforms, and form builders.
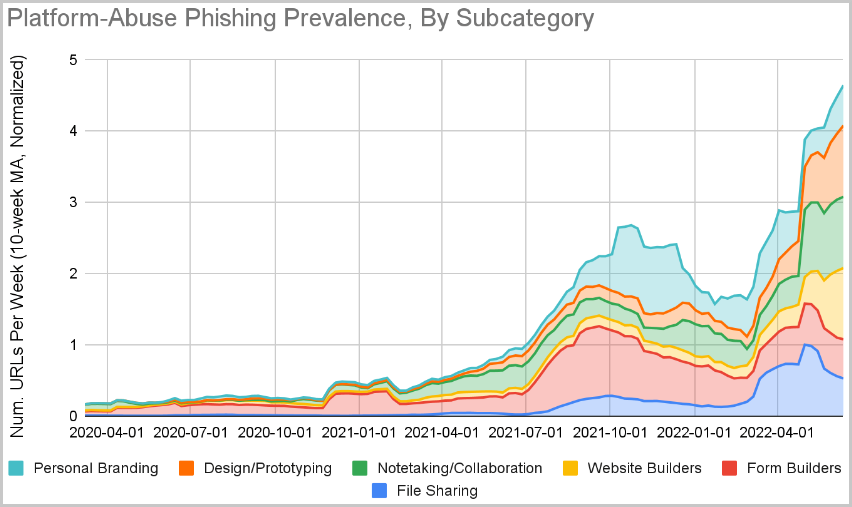
Also, the stats indicate a notable rise in October 2021, based mainly on the sudden uptick in the abuse of form builders.
In 2021, researcher reported about the rampant abuse of "typeform.com" for phishing, an older report from Trend Micro mentioned "123formbuilder.com", "formtools.com", and "smartsurvey.co.uk", while another researcher highlighted the abuse of "Canva.com".
Around the same time, another uptick was spotted, augmented by the abuse of a personal branding site the report doesn't name.
How the services are used
The report explains that in many cases, the phishing actors host their credential stealing pages directly on the abused services, so they send an email to targets containing a URL leading to the page.
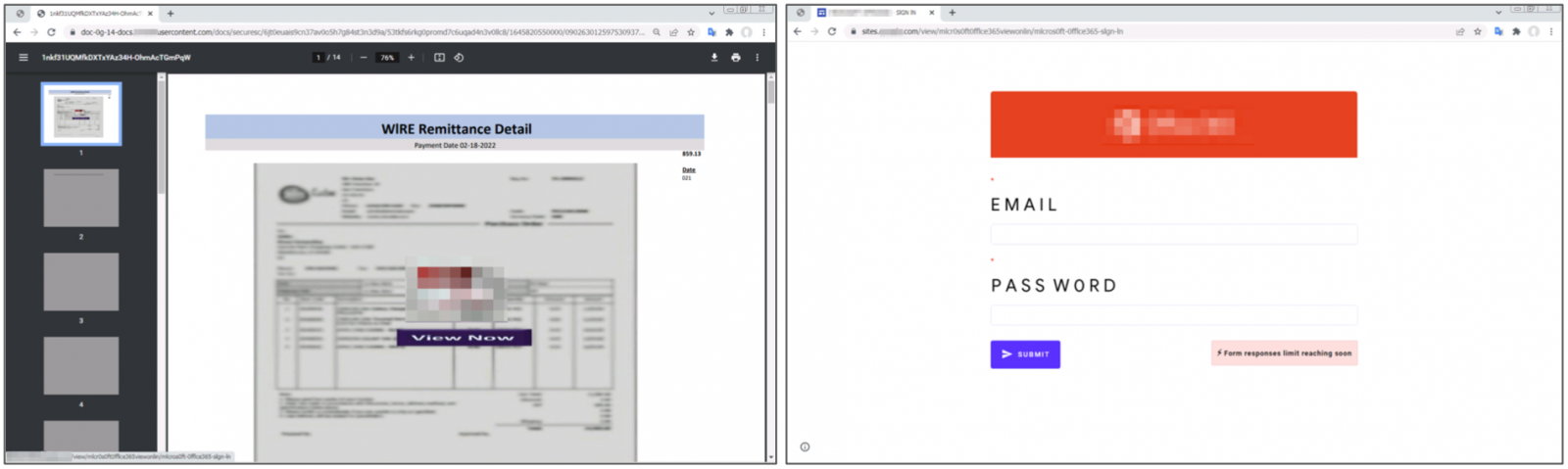
Loading a malicious document from a file hosting service (left), hosting a phishing site (right)
In other cases, however, the landing pages hosted on the abused services don't contain the credential-stealing forms themselves. Instead, they take the victim through one more redirection step to another site.
The phishing site can be hosted on a bulletproof service provider that doesn't respond to takedown requests, so the phishing actors follow that practice to increase campaign uptime while sacrificing the conversion rate.
Even if the phishing page isn't well protected, hiding it behind one more layer reduces the labor required to set everything up again in the case of a takedown.
"In the event that the final credential-stealing page is taken down, the attacker can simply change the link and point to a new credential-stealing page, preserving the effectiveness of the original campaign," reads the report.
Not going away anytime soon
Stopping the abuse of legitimate SaaS platforms will be very hard, as implementing aggressive email filters against those services isn't a choice.
That's precisely what makes them so suitable for phishing campaigns and why the rise in its abuse since last year has been so startling.
If a message that makes bold claims or requests urgent action from you lands in your inbox, avoid clicking embedded links or buttons, but instead use a search engine to locate the official site of the potentially spoofed platform.
Whenever you're requested to enter your account credentials, ensure that you are on the legitimate website URL before you start typing in the form boxes.
A review of zero-day in-the-wild exploits in 2023
28 Mar 2024In 2023, Google observed 97 zero-day vulnerabilities exploited in-the-wild. That’s over 50 percent more than in 2022, but still shy of 2021’s record of 106. Today, Google published its fifth annual review of zero-days exploited in-the-wild.
Read MoreVulnerability In 16.5K+ VMware ESXi Instances Let Attackers Execute Code
25 Mar 2024VMware has acknowledged the presence of several vulnerabilities in its products after they were privately reported.The company has released updates to address these issues in the affected software. While each vulnerability is rated as ‘Important,’ their combined potential impact escalates to ‘Critical’ severity. Shadowserver has tweeted a warning about vulnerabilities in VMware ESXi instances. These vulnerabilities can enable a malicious actor with local admin privileges to bypass sandbox protections. Shadowserver is conducting scans and sharing its findings to help mitigate the risks associated with these vulnerabilities.
Read MoreNIST Cybersecurity Framework 2.0: 4 Steps to Get Started
20 Mar 2024The National Institute of Standards and Technology has revised the book on creating a comprehensive cybersecurity program that aims to help organizations of every size be more secure. Here's where to start putting the changes into action.
Read More