A review of zero-day in-the-wild exploits in 2023

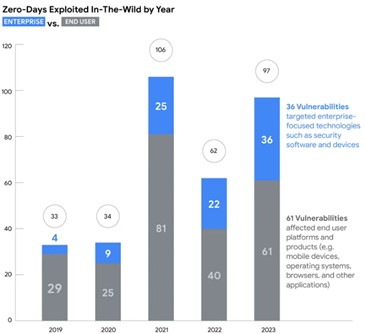
In 2023, Google observed 97 zero-day vulnerabilities exploited in-the-wild. That’s over 50 percent more than in 2022, but still shy of 2021’s record of 106. Today, Google published its fifth annual review of zero-days exploited in-the-wild.
In the report, “We’re All in this Together: A Year in Review of Zero-Days Exploited In-the-Wild in 2023,” released today, we’re taking a broader look at this space with recommendations for others. TAG and Mandiant combined their expertise to analyse zero-days that were actively exploited against both end-user platforms and products (e.g. mobile devices, operating systems, browsers, and other applications) and enterprise-focused technologies such as security software and appliances.
The result, we hope, is not only a broader assessment but clear guidance for others committed to securing the digital world.
When we analyse the data, we see progress in the fight against zero-days. End user platform vendors, such as Apple, Google and Microsoft, have made notable investments that are having a clear impact on the types — and number — of zero-days that actors are able to exploit. Vulnerabilities that were commonplace in years past are virtually non-existent today.
On the enterprise side, we see a wider variety of vendors and products targeted, and an increase in enterprise-specific technologies being exploited. Over the years we’ve learned that the quicker we discover and patch attackers’ bugs, the shorter the lifespan of the exploit, and the more it costs attackers to maintain their capabilities. As an industry, we must now learn how to take those lessons and apply them to the wider ecosystem of vendors that are now finding themselves under attack.
Key Findings from Today’s Report
Vendor investments are making a difference. Notable advancements include Google’s MiraclePtr preventing exploitation of use-after-free vulnerabilities in Chrome, as well as Apple’s introduction of Lockdown mode for iOS, which successfully prevents exploitation of many exploit chains used in-the-wild.
Attackers are now shifting focus to third-party components and libraries in 2023. Zero-day vulnerabilities in third party components and libraries were a prime attack surface in 2023, since exploiting this type of vulnerability can scale to affect more than one product.
Enterprise targeting continues to increase and is more varied in 2023. We observed an increase in adversary exploitation of enterprise-specific technologies in 2023, with a 64 percent increase in the total number of vulnerabilities from the previous year and a general increase in the number of enterprise vendors targeted since at least 2019
Commercial surveillance vendors (CSVs) lead in browser and mobile device exploitation. CSVs were behind 75 percent of known zero-day exploits targeting Google products as well as Android ecosystem devices in 2023 (13 of 17 vulnerabilities). Of the 37 zero-day vulnerabilities in browsers and mobile devices exploited in 2023, we attributed over 60 percent to CSVs that sell spyware capabilities to government customers.
The People’s Republic of China (PRC) continues to lead the way for government-backed exploitation. PRC cyber espionage groups exploited 12 zero-day vulnerabilities in 2023, up from seven in 2022, more than we were able to attribute to any other state and continuing a trend we’ve observed for multiple years.
Exploitation associated with financially motivated actors proportionally decreases. Financially motivated actors accounted for 10 zero-day vulnerabilities exploited in 2023, a lower proportion of the total than what we observed in 2022. Threat group FIN11 exploited three separate zero-day vulnerabilities and at least four ransomware groups separately exploited another four vulnerabilities.
6 recommendations from the report
Exploiting zero-days is no longer a niche capability. The proliferation of exploit technology makes this troubling threat available to more actors around the world. Here are six recommendations for individuals and organizations to improve their security posture.
- One of the biggest ways for industry to help solve the crisis is to embrace transparency and disclosure — sharing lessons and patches publicly, as quickly as possible.
- Organizations need to build defensive strategies that prioritize threats that are most likely to cause damage to themselves and others.
- Build strong security foundations. While this report focuses on zero-days, it’s important to make sure that attackers can’t be successful with simpler attacks. Force them to use zero days by building a strong security foundation.
- Software and product vendors should prepare — during the design phase — for how they will respond when an in-the-wild zero-day is discovered targeting their product. Our recommendations on patching and response from previous years still hold true.
- For high risk users, we suggest enabling Lockdown mode if you’re an iPhone user or Memory Tagging Extensions (MTE) if you use a Pixel
- For Chrome high-risk users, we recommend enabling “HTTPS-First Mode” and disabling the v8 Optimizer.
Protecting end-users
Zero-day research is critical in protecting users and the online ecosystem, which is why we remain committed to our ongoing efforts in the space. Of the 97 unique zero-day vulnerabilities our threat intelligence teams tracked in 2023, 29 were discovered. As always, when we find exploits, we then patch vulnerabilities, share intelligence strategies and fixes with industry peers, and publicly release information about the operations we disrupt. We also use our vulnerability rewards program (VRP) to recognize the contributions of security researchers and we offer a range of tools to help protect high-risk users from online threats.
To protect high risk user accounts, we offer the Advanced Protection Program (APP), which is our highest form of account security and has a strong track record protecting users.
New HardBit Ransomware 4.0 Uses Passphrase Protection to Evade Detection
17 Jul 2024Cybersecurity researchers have shed light on a new version of a ransomware strain called HardBit that comes packaged with new obfuscation techniques to deter analysis efforts.
Read MoreIndonesia tightens cybersecurity after ransomware attack
15 Jul 2024The recent cyberattack in Indonesia, which massively disrupted its national data system, has urged the country to strengthen its cyber resilience and evaluate its digital technology policy, reported Xinhua.
Read MoreNew “Paste and Run” Phishing Technique Makes CTRL-V A Cyber Attack Accomplice
09 Jul 2024A new phishing campaign tries to trick email recipients into pasting and executing malicious commands on their system that installs DarkGate malware.
Read More

