CLOUD APPLICATIONS ARE THE MAJOR CATALYST FOR CYBER-ATTACKS: MICROSOFT

At any point in time on any day of the week, Microsoft’s cloud computing operations are under cyber-attack: The company detects a whopping 1.5 million attempts a day to compromise its systems. The increased number of ransomware attacks begins with cybercriminals exploiting common cybersecurity errors, and breaching cloud applications which – if correctly managed – could prevent most victims from falling prey to attacks.
Microsoft analyzed anonymized data of real cyber threat activity and, according to the company’s fresh Cyber Signals report, found that over 80% of ransomware attacks can be traced to common configuration errors in software and devices. These consist of applications being left in their default state, allowing user-broad access across the network, security tools being left untested or misconfigured, cloud applications set up in a way that unauthorized intruders are easily getting permission to gain access, and organizations not applying Microsoft’s attack surface reduction rules, which allows attackers to run malicious code using macros and scripts. It’s these misconfigurations that ransomware attackers are looking for as they seek out vulnerable targets for cyber-attacks – often with the added threat of double extortion attacks, where cyber criminals steal sensitive data and threaten to publish it if their demands are not being paid.
Attackers have only been able to get into such as strong position because those responsible for defending networks don’t always have a full grasp on what they’re managing. On the other hand, Microsoft is not only fending off those attacks but also learning from them. All those foiled cyber-attacks, along with data about the hundreds of billions of emails and other pieces of information that flow to and from Microsoft’s cloud computing data centers, are constantly being fed into the company’s intelligent security graph. It’s a massive web of data that can be used to connect the dots between an email phishing scam out of Nigeria and a denial-of-service attack out of Eastern Europe, thwarting one attack for one customer and applying that knowledge to every customer using products including the company’s Azure cloud computing platform, Windows 10 operating system or Office 365 productivity service.
Dmitri Alperovitch, co-founder and former CTO of CrowdStrike presented his view “That’s what people often misunderstand about attacks – they don’t happen at the speed of light, it often takes months or years to get the right level of access in a network and ultimately to be able to push the trigger and cause a destructive act,”. That might appear like obvious advice, but in many cases, cyber-criminal and nation-state hackers have broken into corporate networks and remained there for a long time without being detected. Some of these campaigns call for intrusions into critical infrastructure where malicious hackers carry out damage which might turn into serious consequences in terms of cyber security. And going through deep knowledge of the Cloud applications network and being able to detect any suspicious or unexpected behavior seems the only way that can go a long way to detect and stop intrusions. “Defence can work if you have time. If you’re looking inside your systems, hunting for adversaries and applying intelligence, you’re able to discover them even if they get in before they do any damage,” Alperovitch adds.
Those cybersecurity threats have sky-high substantially in recent because criminals have built lucrative businesses from stealing data and nation-states have come to see cybercrime as an opportunity to acquire information, influence, and advantage over their rivals. This has made a path for potential catastrophic attacks such as the WannaCrypt ransomware campaign which was being displayed in recent headlines. This evolving threat landscape has begun to change the way customers view the cloud. “It was only a few years ago when most of my customer conversations started with, ‘I can’t go to the cloud because of security. It’s not possible,’” said Julia White, Microsoft’s corporate vice president for Azure and security. “And now I have people, more often than not, saying, ‘I need to go to the cloud because of security.’”
It’s not an exaggeration to say that cloud computing is completely changing our society. It’s ending major industries such as the retail sector, enabling the type of mathematical computation that is uplifting an artificial intelligence revolution and even having a profound impact on how we communicate with friends, family, and colleagues.
On the one hand, individuals and companies have had to give up a measure of physical control that comes from knowing all their emails and family photos are on the hard drive of their home computer in the living room, and all their sales or payroll data are stored on servers physically located within company offices. But on the other hand, security experts say, the cloud has allowed companies like Microsoft to create much more sophisticated tools to guard against increasingly cunning attackers. That means instead of having to manage security completely on their own, companies also can rely on cloud service providers like Microsoft who have only one job — to keep your data secure.
Each organization should apply security patches and updates as quickly as possible to prevent cyber-attack and attackers from being able to exploit known vulnerabilities.
A review of zero-day in-the-wild exploits in 2023
28 Mar 2024In 2023, Google observed 97 zero-day vulnerabilities exploited in-the-wild. That’s over 50 percent more than in 2022, but still shy of 2021’s record of 106. Today, Google published its fifth annual review of zero-days exploited in-the-wild.
Read MoreVulnerability In 16.5K+ VMware ESXi Instances Let Attackers Execute Code
25 Mar 2024VMware has acknowledged the presence of several vulnerabilities in its products after they were privately reported.The company has released updates to address these issues in the affected software. While each vulnerability is rated as ‘Important,’ their combined potential impact escalates to ‘Critical’ severity. Shadowserver has tweeted a warning about vulnerabilities in VMware ESXi instances. These vulnerabilities can enable a malicious actor with local admin privileges to bypass sandbox protections. Shadowserver is conducting scans and sharing its findings to help mitigate the risks associated with these vulnerabilities.
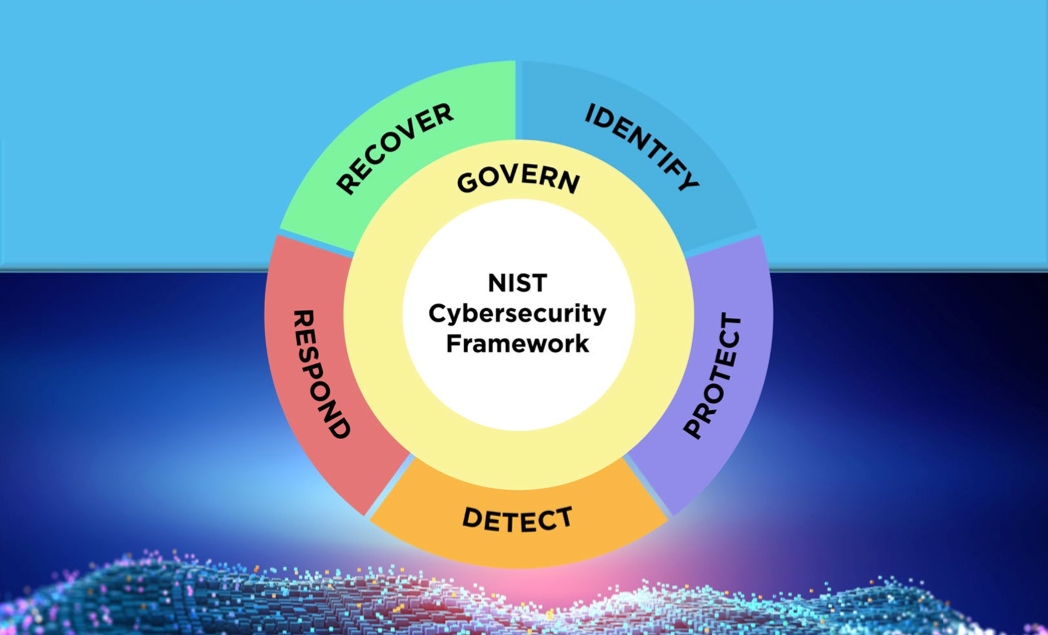
Read MoreNIST Cybersecurity Framework 2.0: 4 Steps to Get Started
20 Mar 2024The National Institute of Standards and Technology has revised the book on creating a comprehensive cybersecurity program that aims to help organizations of every size be more secure. Here's where to start putting the changes into action.
Read More