CLR SqlShell Malware Targets MS SQL Servers for Crypto Mining and Ransomware
Poorly managed Microsoft SQL (MS SQL) servers are the target of a new campaign that's designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of cryptocurrency miners and ransomware.
"Similar to web shell, which can be installed on web servers, SqlShell is a malware strain that supports various features after being installed on an MS SQL server, such as executing commands from threat actors and carrying out all sorts of malicious behaviour," security researcher said last week.
A stored procedure is a subroutine that contains a set of Structured Query Language (SQL) statements for use across multiple programs in a relational database management system (RDBMS).
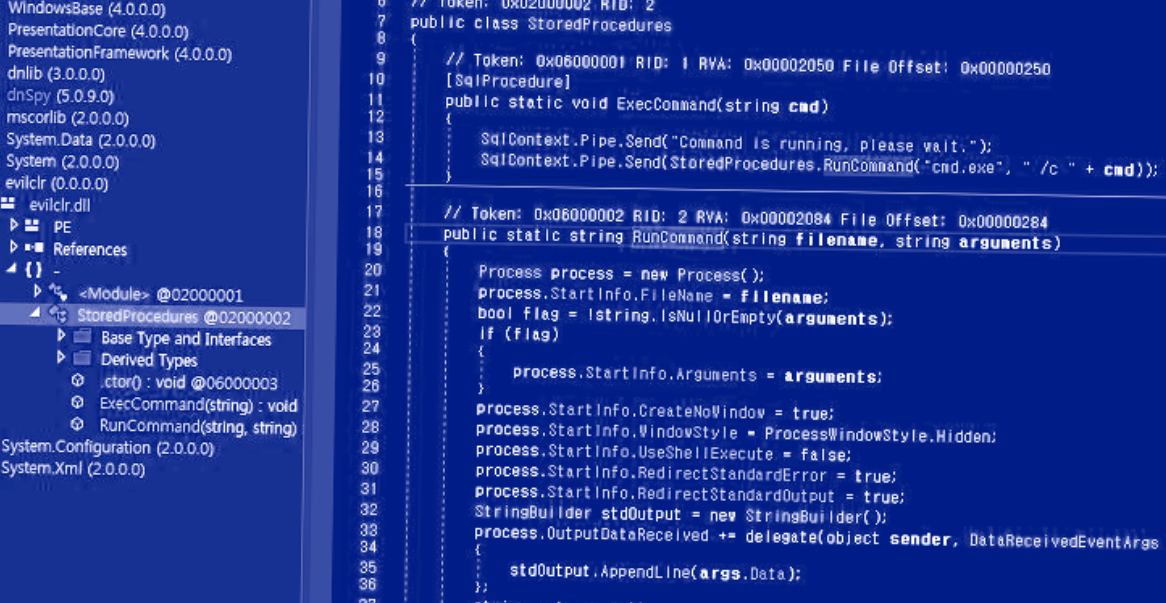
CLR (short for common language runtime) stored procedures – available in SQL Server 2005 and later – refer to stored procedures that are written in a .NET language such as C# or Visual Basic.
The attack method discovered by the South Korean cybersecurity firm entails the use of CLR stored procedure to install the malware in MS SQL servers using the xp_cmdshell command, which spawns a Windows command shell and passes an instruction as input for execution.
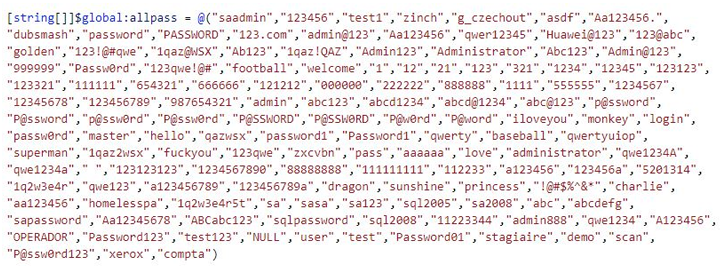
Some of the techniques employed by threat actors, including those associated with LemonDuck, MyKings (aka DarkCloud or Smominru), and Vollgar, concern the exploitation of internet-exposed MS SQL servers via brute-force and dictionary attacks to run xp_cmdshell commands and OLE stored procedures and execute malware.
The use of CLR stored procedures is the latest addition to this list, with attackers taking advantage of SqlShell routines to download next-stage payloads such as Metasploit and cryptocurrency miners like MrbMiner, MyKings, and LoveMiner.
What's more, SqlShells named SqlHelper, CLRSQL, and CLR_module have been used by different adversaries to escalate privileges on compromised servers and launch ransomware, proxyware, and incorporate capabilities to carry out reconnaissance efforts in targeted networks.
"SqlShell can install additional malware such as backdoors, coin miners, and proxyware, or it can execute malicious commands received from threat actors in a way similar to WebShell," researcher said.
A review of zero-day in-the-wild exploits in 2023
28 Mar 2024In 2023, Google observed 97 zero-day vulnerabilities exploited in-the-wild. That’s over 50 percent more than in 2022, but still shy of 2021’s record of 106. Today, Google published its fifth annual review of zero-days exploited in-the-wild.
Read MoreVulnerability In 16.5K+ VMware ESXi Instances Let Attackers Execute Code
25 Mar 2024VMware has acknowledged the presence of several vulnerabilities in its products after they were privately reported.The company has released updates to address these issues in the affected software. While each vulnerability is rated as ‘Important,’ their combined potential impact escalates to ‘Critical’ severity. Shadowserver has tweeted a warning about vulnerabilities in VMware ESXi instances. These vulnerabilities can enable a malicious actor with local admin privileges to bypass sandbox protections. Shadowserver is conducting scans and sharing its findings to help mitigate the risks associated with these vulnerabilities.
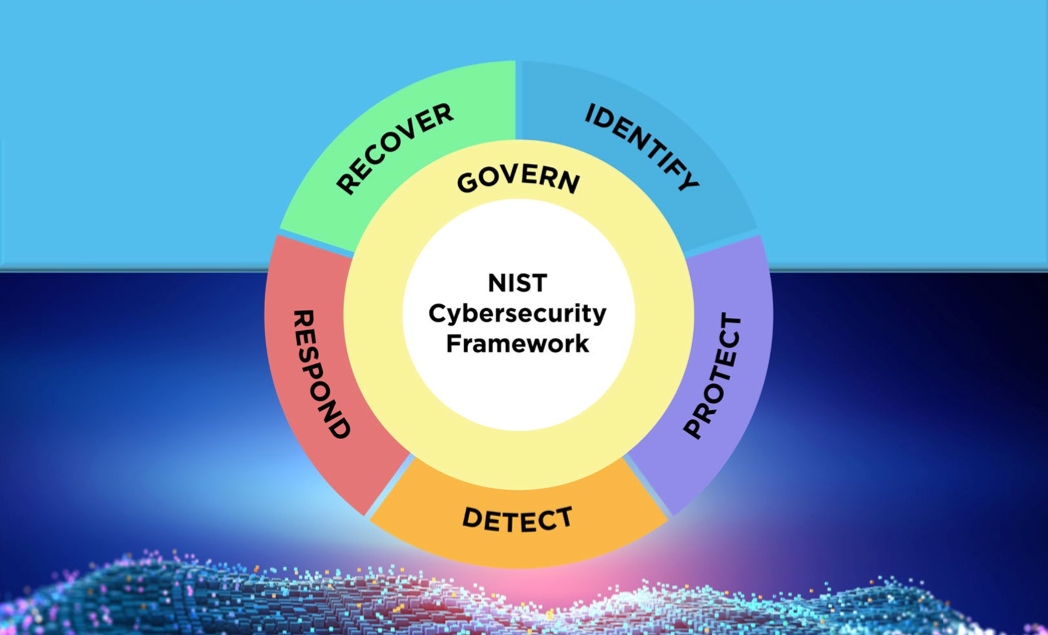
Read MoreNIST Cybersecurity Framework 2.0: 4 Steps to Get Started
20 Mar 2024The National Institute of Standards and Technology has revised the book on creating a comprehensive cybersecurity program that aims to help organizations of every size be more secure. Here's where to start putting the changes into action.
Read More