Phishing drops IceXLoader malware on thousands of home, corporate devices

An ongoing phishing campaign has infected thousands of home and corporate users with a new version of the 'IceXLoader' malware.
The authors of IceXLoader, a malware loader first spotted in the wild this summer, have released version 3.3.3, enhancing the tool’s functionality and introducing a multi-stage delivery chain.
The discovery of the Nim-based malware came in June 2022, when IceXLoader was in version 3.0, but the loader was missing key features and generally appeared like a work-in-progress.
Security researcher published a new post on Tuesday, warning that the latest version of IceXLoader marks a departure from the project’s beta development stage.
For a malware loader so aggressively promoted on the cybercrime underground, any development of this kind is significant and could lead to a sudden uptick in its deployment.
Current Delivery Chain
The infection begins with the arrival of a ZIP file via a phishing email containing the first-stage extractor.
The extractor creates a new hidden folder (.tmp) under “C:\Users\<username>\AppData\Local\Temp” and drops the next-stage executable, ‘STOREM~2.exe.’
Then, depending on the extract settings selected by the operator, the infected system may be rebooted, and a new registry key will be added to delete the temp folder when the computer restarts.
The dropped executable is a downloader that fetches a PNG file from a hardcoded URL and converts it into an obfuscated DLL file which is the IceXLoader payload.
After decrypting the payload, the dropper performs checks to ensure it’s not running inside an emulator and waits 35 seconds before executing the malware loader to evade sandboxes.
Finally, IceXLoader is injected into the STOREM~2.exe process using process hollowing.
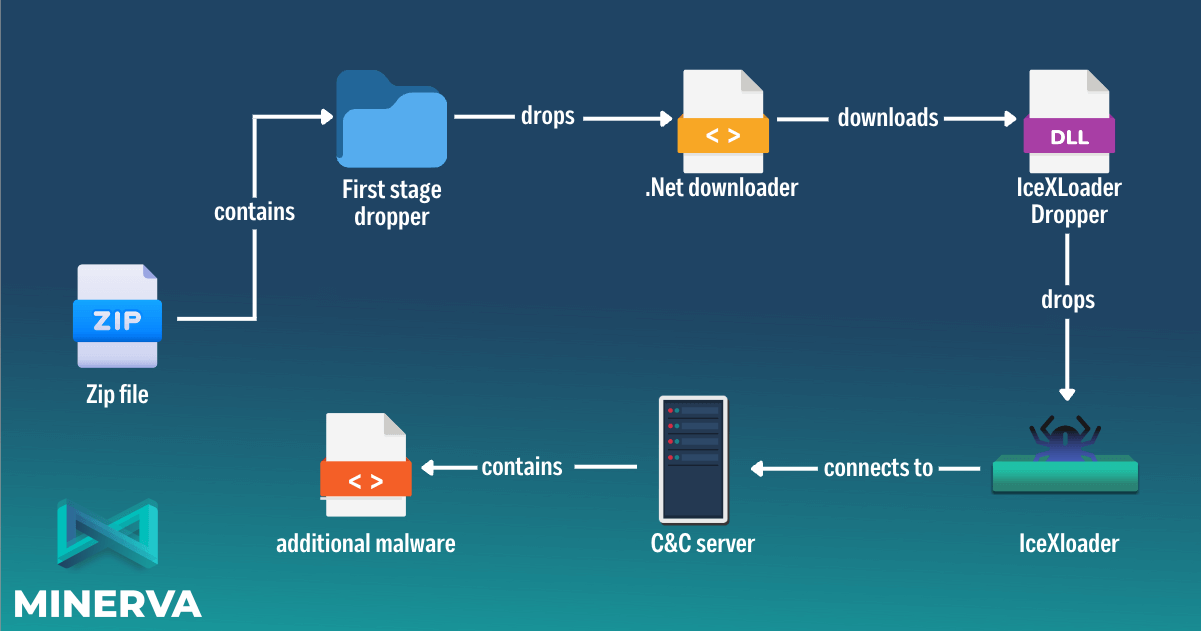
The complete IceXLoader infection chain
New IceXLoader
Upon the first launch, IceXLoader version 3.3.3 copies itself into two directories named after the operator’s nickname and then collects the following information about the host and exfiltrates it to the C2:
- IP address
- UUID
- Username and machine name
- Windows OS version
- Installed security products
- Presence of .NET Framework v2.0 and/or v4.0
- Hardware information
- Timestamp
To ensure persistence between reboots, the malware loader also creates a new registry key at “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.”
For evasion, it uses a method of in-memory patching in AMSI.DLL, bypassing the Microsoft Windows Antimalware Scan Interface used by Windows Defender and other security products.
“The loader also creates and executes a .bat file which disables Windows Defender’s real-time scan and also adds exclusions to Windows Defender to prevent it from scanning the directory IceXLoader was copied to.” – Security researcher said.
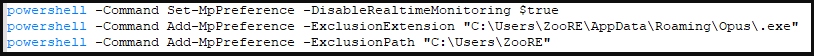
PowerShell commands to disable AV and add exemptions
The commands supported by the loader are the following:
- Stop execution
- Collect system info and exfiltrate to C2
- Display dialog box with specified message
- Restart IceXLoader
- Send GET request to download a file and open it with “cmd/ C”
- Send GET request to download an executable to run it from memory
- Load and execute a .NET assembly
- Change C2 server beaconing interval
- Update IceXLoader
- Remove all copies from the disk and stop running
Researcher reports that the threat actors behind this campaign aren’t interested in securing the stolen data, as the SQLite database holding stolen information is accessible in the C2 address.
The exposed database contains records corresponding to thousands of victims, containing a mix of home PC and corporate PC infections.
The security researchers have informed the affected companies of the exposure, but the database is updated with new entries daily.
A review of zero-day in-the-wild exploits in 2023
28 Mar 2024In 2023, Google observed 97 zero-day vulnerabilities exploited in-the-wild. That’s over 50 percent more than in 2022, but still shy of 2021’s record of 106. Today, Google published its fifth annual review of zero-days exploited in-the-wild.
Read MoreVulnerability In 16.5K+ VMware ESXi Instances Let Attackers Execute Code
25 Mar 2024VMware has acknowledged the presence of several vulnerabilities in its products after they were privately reported.The company has released updates to address these issues in the affected software. While each vulnerability is rated as ‘Important,’ their combined potential impact escalates to ‘Critical’ severity. Shadowserver has tweeted a warning about vulnerabilities in VMware ESXi instances. These vulnerabilities can enable a malicious actor with local admin privileges to bypass sandbox protections. Shadowserver is conducting scans and sharing its findings to help mitigate the risks associated with these vulnerabilities.
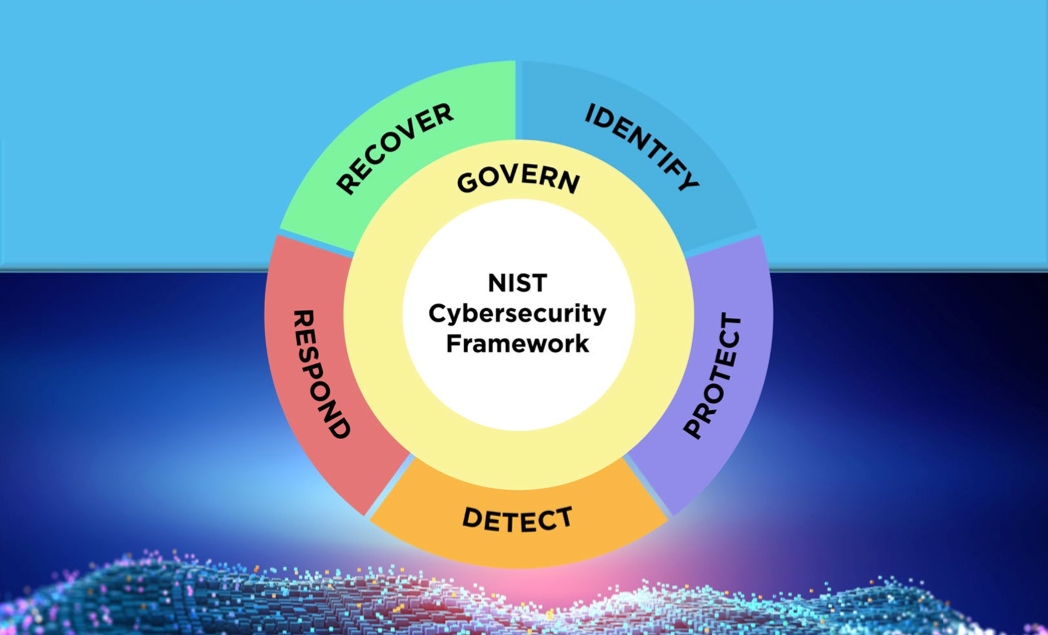
Read MoreNIST Cybersecurity Framework 2.0: 4 Steps to Get Started
20 Mar 2024The National Institute of Standards and Technology has revised the book on creating a comprehensive cybersecurity program that aims to help organizations of every size be more secure. Here's where to start putting the changes into action.
Read More