Why Zero Trust Should be the Foundation of Your Cybersecurity Ecosystem

For cybersecurity professionals, it is a huge challenge to separate the "good guys" from the "villains". In the past, most cyberattacks could simply be traced to external cybercriminals, cyberterrorists, or rogue nation-states. But not anymore.
Threats from within organizations – also known as "insider threats" – are increasing and cybersecurity practitioners are feeling the pain.
Traditional perimeter defenses are not designed to prevent these attacks. They also struggle to keep external attackers out. Clever hackers continuously find ways in and "weaponize" their trusted status inside the network to compromise sensitive assets and orchestrate larger attacks.
And an increasing number of enterprise resources – applications, devices, data, and even people – now live outside the perimeter. It's difficult to protect these assets with legacy approaches, much less fortify the perimeter to keep attackers out completely.
How can you protect your organization in this landscape?
The answer: Adopt a zero trust approach to cybersecurity.
What is Zero Trust?
The traditional perimeter relies on a "trust but verify" approach where all users and endpoints are automatically trusted once they are "in" the network. But as we have seen, this method creates serious security risks, both from malicious internal actors and from external actors compromising legitimate credentials.
Zero trust aims to eliminate this risk with its "trust nothing, verify everything" approach. It involves continuously monitoring and validating the privileges of each user and device along with vetting all access requests before allowing that user or device to access an enterprise asset.
The Growth of Zero Trust
Recently, zero trust has developed a large following due to a surge in insider attacks and an increase in remote work – both of which challenge the effectiveness of traditional perimeter-based security approaches.
A 2021 global enterprise survey found that 72% respondents had adopted zero trust or planned to in the near future. Gartner predicts that spending on zero trust solutions will more than double to $1.674 billion between now and 2025.
Governments are also mandating zero trust architectures for federal organizations. These endorsements from the largest organizations have accelerated zero trust adoption across every sector. Moreover, these developments suggest that zero trust will soon become the default security approach for every organization.
Should You Adopt Zero Trust?
Zero trust enables organizations to protect their assets by reducing the chance and impact of a breach. It also reduces the average breach cost by at least $1.76 million, can prevent five cyber disasters per year, and save an average of $20.1 million in application downtime costs.
However, deciding to embrace zero trust is much easier than actually implementing it. For many organizations, the transition process can be both overwhelming and labor-intensive.
Implementing zero trust with an extended detection and response (XDR) platform can provide a far greater fabric of security than using either one alone. And by combining multiple defenses such as threat prevention, detection, and automated response, XDR provides a strong foundation to a zero trust strategy.
Zero trust is possible without XDR. But with XDR, it's much harder for bad actors to breach your systems or compromise your mission-critical assets.
A review of zero-day in-the-wild exploits in 2023
28 Mar 2024In 2023, Google observed 97 zero-day vulnerabilities exploited in-the-wild. That’s over 50 percent more than in 2022, but still shy of 2021’s record of 106. Today, Google published its fifth annual review of zero-days exploited in-the-wild.
Read MoreVulnerability In 16.5K+ VMware ESXi Instances Let Attackers Execute Code
25 Mar 2024VMware has acknowledged the presence of several vulnerabilities in its products after they were privately reported.The company has released updates to address these issues in the affected software. While each vulnerability is rated as ‘Important,’ their combined potential impact escalates to ‘Critical’ severity. Shadowserver has tweeted a warning about vulnerabilities in VMware ESXi instances. These vulnerabilities can enable a malicious actor with local admin privileges to bypass sandbox protections. Shadowserver is conducting scans and sharing its findings to help mitigate the risks associated with these vulnerabilities.
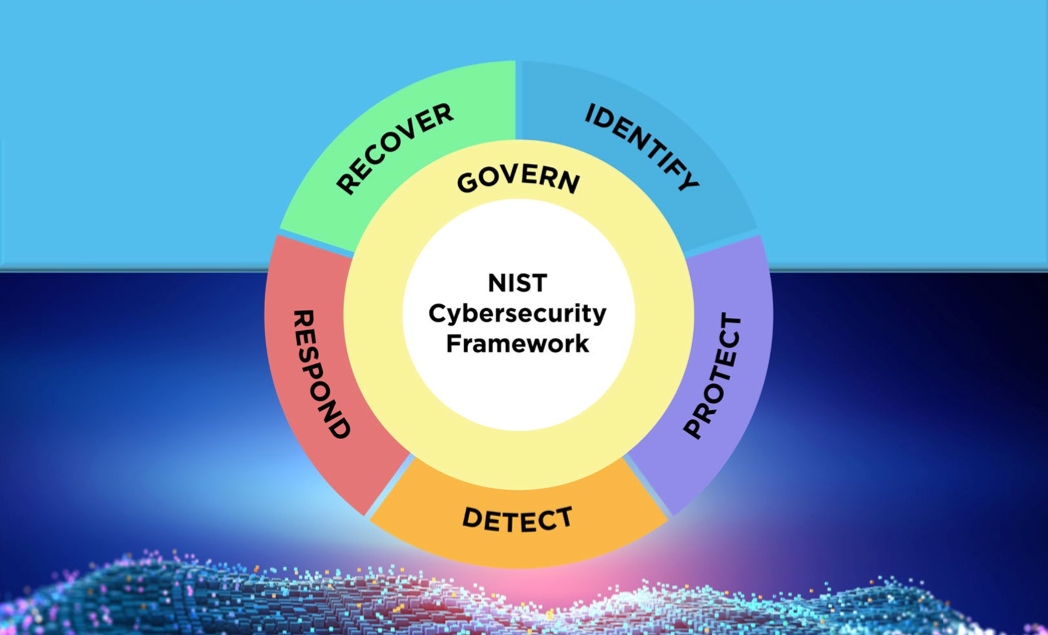
Read MoreNIST Cybersecurity Framework 2.0: 4 Steps to Get Started
20 Mar 2024The National Institute of Standards and Technology has revised the book on creating a comprehensive cybersecurity program that aims to help organizations of every size be more secure. Here's where to start putting the changes into action.
Read More